Many types of malware and clever hackers are lurking around, and you have to secure your data and devices from them.
Table of Contents
- Use strong passwords wisely
- Use two-factor authentication
- Be aware of phishing
- Think twice before you click
- Optimize your privacy settings if necessary
- Don’t post too much personal information
- Use a VPN
- Don’t visit non-HTTPS websites
- Keep systems and apps up-to-date
- Never leave devices unattended
- Install apps carefully
- Install an antivirus and scan your devices often
- Use an admin account only if necessary
- Take advantage of a firewall
- Clear the cache and browsing records often
- Organize your files often
- Use multiple email addresses
- Disable location services as much as possible
- Be overly vigilant
- Wipe old devices before disposing
- Look for signs of being hacked
- Keep backups of all important data
1. Use Strong Passwords Wisely
The first obstacle of the hacker’s way of stealing your data is your password. A password is your key to the account, and you have every reason not to expose it to others. However, hackers and malware have many ways to crack a password. Here are just some of them.
Therefore, maintaining passwords are essential to online safety. Never use common sequences of characters such as “123456” or “qwerty” because they are overused and are the first passwords hackers guess in a brute-force attack.
Moreover, making it long is essential. If it’s too short, hackers can go through all combinations with ease. Choose a password no shorter than 12 characters, and use a random password generator to avoid any patterns.
Furthermore, do not include personal information on a password. If that’s the case, hackers can use personal information to come up with a series of passcodes, and one of which might be your actual password. Remember to produce unique passwords, which prevents your account from being accessed due to a breached password on another account.

Image Credit: Canva
If you can come up with a strong password quickly and at any time, change your passwords regularly. But if you’re afraid you can’t, play it safe and only change your passwords in case of a data breach.
2. Use Two-factor Authentication
Using your password as the only fence between hackers and your data isn’t quite secure. Therefore, we need other forms of authentication, including a verification code or your biometrics, such as your fingerprints.
For instance, other than a password, a Google account can use a six-digit verification code. This code is obtained from an SMS message, a phone call, or the Google Authenticator app. Google account owners can also use a security key to get in.

Image Credit: Canva
3. Be Aware of Phishing
Spam emails and messages are harmful because they might intend to install malware or steal your personal information. Thus, you should be able to filter out spam successfully. Fortunately, some features can help you indicate the message or email is indeed spam.
If the message makes you panic and asks you to confirm your personal information, it’s likely fake. The only purpose it can go this way is to scare you and let your guard down to make it more likely for you to click on the link and provide the personal information.
Secondly, you have to look at the email address carefully. If the email is sent by Microsoft, it should have a sender email address that should contain “@microsoft.com” If it doesn’t, it must be a fake email, regardless of how authoritative it sounds. Emails from legitimate companies never come from unknown or messy email addresses.
Thirdly, generic greetings are often signs that a message is spam. If it’s a person or a company that knows you, they should include your name or username in the email/message. If it’s too generic (e.g., Dear Customer), it’s probably a sign that it’s not a company you signed up for.
On the other hand, you should look for misspellings and grammatical mistakes. Scammers deliberately do so because they want to bypass the spam filters and let the email land straight at your inbox. As a result, you should carefully look for minor errors in the message body and be extra careful when you spot an excessive amount of flaws, especially if accompanied with other symptoms.

Image Credit: Canva
If you’ve noticed that an email is spam, make sure to delete it and report the scammer. If the scammer is your friend, call him/her immediately because their accounts may be hacked.
4. Think Twice Before You Click
Often, phishing emails or messages contain links and attachments. They are the primary purpose of sending the spam email and is the only way for hackers to install malware or acquire personal data from an email. Remember to use the clues above the judge whether the message is spam or not.
However, there’s one more step before you click: Hover your mouse on it. In your browser, you should see the destination URL of the link. You should look at that carefully to see if there are any abnormalities. If the URL is weird, you’d better dodge this website and delete the message. Insignificant differences like an “l” turning into a “1” can mean the difference between a safe or dangerous website, so you should search for them, too.
If you’re faced with an account issue in your email, it’s best not to click the link no matter where it heads you for, and directly insert the URL and log in to your account instead. That way, you can see if the issue mentioned in the email is genuine or not.
5. Optimize Privacy Settings if Necessary
Sometimes, the default settings aren’t the most secure set of options. Therefore, you should look at the privacy settings and make changes if necessary. For instance, you can manage who can see your posts. Some prefer posts to be open to the public, while others only allow approved followers to see the posts.
Moreover, you can limit what the platform knows about you. For example, you should not include location information in your posts. You should also limit the information you share on your profile. Anything non-required, including your location and your birthday, isn’t worth inserting unless it is an organization. Besides securing your posts and information, some settings can make a more pleasant online experience, too.
6. Don’t Post Too Much Personal Information
Other than protecting your posts, it’s best to think twice before you upload something on social media, whether they’re pictures or some text. When you’re about to hit the button to post, be careful. Your post should not contain excessively personal or sensitive information, including confidential documents or your address.
As you know, providing too much information to strangers is dangerous, and one of the biggest threats of oversharing is spear-phishing. Instead of having hundreds or thousands of targets, a spear-phishing campaign only focuses on one target and researches his/her personal information as much as possible. Then, they will customize an email to look as legitimate as possible and try to indirectly convince the target to click on the link and fall into a trap.

Image Credit: Canva
7. Use a VPN
A VPN (Virtual Private Network) essentially sends your requests to a VPN server, and it’s the servers that are really sending the requests to the target website. In that case, you can obscure your actual IP address. It also encrypts your data so that no one else can see your messages in the encrypted tunnel unless they have the correct decryption key.
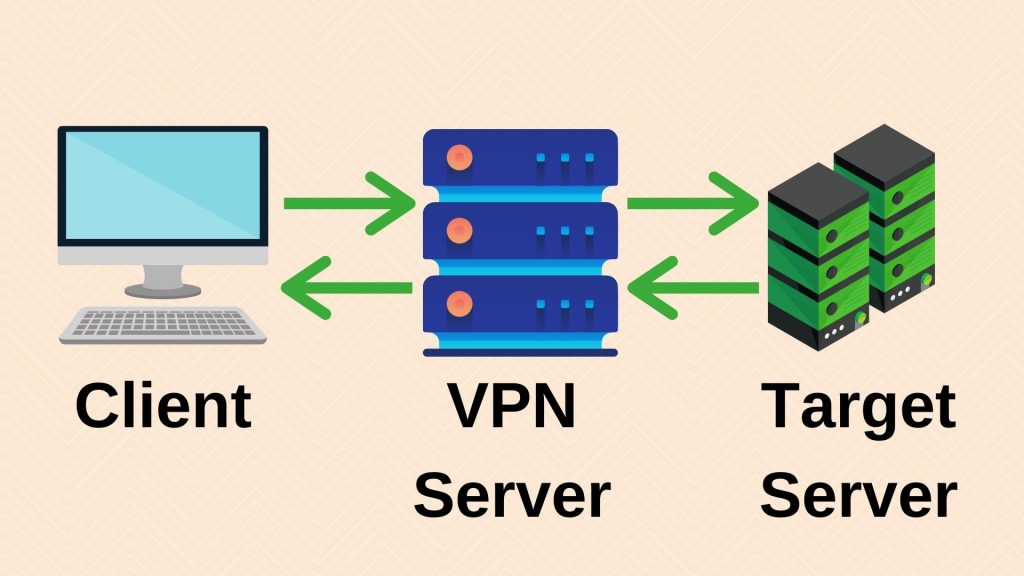
Image Credit: Canva
Other than the security they can provide, VPNs can also let you watch location-restricted content. This is a workaround that can allow you to explore more, too!
8. Don’t Visit non-HTTPS Websites
Nowadays, using just HTTP is an insecure practice. Instead, your site should have HTTPS to make a good browsing experience. You only need a TLS certificate to let your visitors enjoy the numerous benefits that this more secure protocol provides. TLS encrypts (and decrypts) your message using a private key on your server and a public key on your browser to make your messages invisible to any strangers that are intercepting the network.
Therefore, it isn’t nice to visit non-HTTPS sites, especially if sensitive information like passwords is entered. Also, if you own a website that does not have HTTPS, obtain a TLS certificate immediately. This should be the first thing to do once the site is online.
9. Keep Systems and Apps Up-to-date
When you receive a notification about an update, click “Update” at once. Although it may take a few minutes, it’s worth it. This is because software updates often fix bugs that can cause let hackers spy on your information or infect the computer with malware. When an update is released, cybercriminals may already be actively exploiting the weaknesses of the system! In that case, it’s pointless to not to update, right?
10. Never Leave Devices Unattended
Imagine that your device is not in use by anybody and is still on! In that case, anyone passing by could use your computer. For instance, the US Strategic Command’s Twitter manager left his computer for a short time, but that’s enough for his child to play with the keyboard and accidentally posted a strange message which led to speculations that the account was hacked.
Therefore, if you’re getting out from your device, you should turn it off. If your computer is suffering from an attack, turning off the computer can undoubtedly stop it. However, if it’s not worth it to shut down the computer and boot the OS, lock the computer. It can do most of the job as it does not allow access unless the user knows the password.
11. Install Apps Carefully
Is it secure to install an app from an unknown website? No, it’s not. Make sure that you install apps from official sources like a reputable app store or its official website. Moreover, you should read the reviews, and don’t install one if there are too many bad grades especially if all the bad opinions are focused on one part of the app.
12. Install An Antivirus and Scan Your Devices Often
To ensure the security of your computer, installing an antivirus is a must. You can’t detect every single type of malware with your naked eye. Sometimes, they’re just doing their things too sneakily and don’t make any visible changes at all. Although an antivirus still misses some malware because they can bypass the layer of protection, it is much better than observing signs of being infected through your naked eye.
Fortunately, if you’re using Windows, you should have a built-in antivirus called Windows Security, so you don’t need an extra one unless you think it isn’t good enough.
However, just installing an antivirus is not enough. Ideally, you should scan your computer daily if you are using it frequently. Other than quick scans that only look for malware on essential parts, it’s best to regularly run full scans, which puts the scan function to its full potential. Essentially, that’s like a thorough health checkup of the whole system, including removable drives.
13. Use An Admin Account Only if Necessary
You shouldn’t treat your admin account as your primary account. In fact, only use an admin account if necessary. That means if whatever you do does not require admin privileges, use your standard account instead of an admin account. If you’re an admin with only one account, create a standard account immediately and migrate your data there.
After reading the last paragraph, you may wonder why you should do so. That’s because if malware is installed into your admin account, it has a higher level of permission and can do whatever they want to do to the system. However, malware infecting a standard user account can only modify a limited amount of the system, and therefore, it’s easier to recover in that case.
14. Take Advantage of a Firewall
Many online attacks trying to steal your data come from some malicious network connection. That’s where a firewall can come into play. Firewalls scan packets of your online traffic and block malicious messages so that your computer cannot get an attack. Therefore, using a firewall is important to protect your data.
15. Clear the Cache and Browsing Records Often
If your computer needs to be used by other people (especially if you’re using a public computer), make sure you clear your browsing footprints! If you don’t, the people that use the computer after you might be able to see your browsing records. The data could be used for stealing sensitive information or even assisting a spear-phishing campaign!
16. Organize Your Files Often
Other than deleting unnecessary browsing data, you should remove obsolete files. You may ask, “How is that related to cybersecurity?” Organizing files not only tidies up your computer to find important files more easily, but it also reveals unknown files. If a file on your account that isn’t created by you or with your permission exists, it’s a clear sign that someone broke into your computer. Make sure to search the filename online before drawing a conclusion.
17. Use Multiple Email Addresses
If you want to prevent online attacks from accessing all your files, use multiple email addresses. Generally, it can separate work and leisure accounts. On the other hand, another email address can also act as a backup in case something goes wrong with the main address. It could be anywhere from a forgotten password to a hacked account.
18. Disable Location Services as Much as Possible
Moreover, remember to disable location services whenever it’s not necessary. Exposing your current location can lead to some severe consequences. This includes location-related spear-phishing, which might make the fake message sound even more legitimate.
Moreover, location can be used to serve ads. While the algorithm is designed to make your browsing experience better, some people don’t want servers to know that much about you. Normally, the cybercriminals cannot get the location data of users. But what if a data breach occurs? That opens up the chances of it being used for illegal purposes significantly.
19. Be Overly Vigilant
When you communicate with someone online, you should be very careful. Even if this person is your trusted coworker or friend, you never know when their accounts are hacked, and a scammer is standing right behind the screen. Therefore, if you see any abnormalities in messages from people you know, immediately contact the sender because these messages might not be sent by him/her.
20. Wipe Old Devices Before Disposing
Want to sell or recycle your old computers or phones? Make sure you wipe it clean first. By doing so, you can prevent your data from being stolen from your hard drive. What’s more, it reduces the inconvenience by the other user as they can just set up the operating system by themselves and can omit the reset process, right?
However, if there are options in the erase process, make sure you choose the most secure one. That means it wipes the hard drive as many times as possible. This makes it extremely difficult for data recovery experts to extract information from your old storage device.
21. Look for Signs of Being Hacked
No matter how well you’ve done the last 20 tips above, hackers are still able to come up with ways to steal your data and infect your devices. Therefore, you should search for signs of being hacked. Here are some symptoms:
- There are strange online activities
- You lost control of your input devices
- Your password doesn’t work suddenly
- Unknown files are added
- Apps and/or your antivirus is/are disabled
- Your computer suddenly works too slowly
- There are strange online activities
- There are posts, emails, or messages that you didn’t send
- You receive messages stating that your computer or accounts are hacked
22. Keep Backups of All Important Data
Last but not least, keep backups of your files, documents, pictures, and all other important files. If anything goes wrong and some data is lost, you can restore it using your backup. Ideally, you should make two or more backups both in the cloud and on an external hard drive.
If you don’t have a backup, you risk permanently losing your data. If it’s a business, not backing up can cause adverse outcomes or even cause organizations to stop working!
Conclusion
In this article, we talked about 22 tips to secure your data and devices so that you don’t get hacked (or get hacked less often). There are more to learn, and you should visit the websites in the references below.
References and Credits
- Charlotte Empey. (2018, August 15). How to Create a Strong Password. Retrieved May 5, 2021, from https://blog.avast.com/strong-password-ideas
- Clifford Colby, Sharon Profis. (2020, August 6). 9 rules for strong passwords: How to create and remember your login credentials. Retrieved May 5, 2021, from https://www.cnet.com/how-to/9-rules-for-strong-passwords-how-to-create-and-remember-your-login-credentials/
- Google Account Help. (n.d.). Create a strong password & a more secure account. Retrieved May 5, 2021, from https://support.google.com/accounts/answer/32040?hl=en
- Google. (n.d.). Google 2-Step Verification. Retrieved May 5, 2021, from https://www.google.com/landing/2step/
- Seth Rosenblatt, Jason Cipriani. (2015, June 15). Two-factor authentication: What you need to know (FAQ). Retrieved May 5, 2021, from https://www.cnet.com/news/two-factor-authentication-what-you-need-to-know-faq/
- Mike James. (2018, August 22). 5 Ways to Spot a Phishing Email. Retrieved May 5, 2021, from https://staysafeonline.org/blog/5-ways-spot-phishing-emails/
- Consumer Information | Federal Trade Commission. (n.d.). How to Recognize and Avoid Phishing Scams. Retrieved May 5, 2021, from https://www.consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams
- National Cyber Security Alliance. (n.d.). Social Media. Retrieved May 6, 2021, from https://staysafeonline.org/stay-safe-online/securing-key-accounts-devices/social-media/
- Kaspersky. (n.d.). What is Spear Phishing? Retrieved May 6, 2021, from https://www.kaspersky.com/resource-center/definitions/spear-phishing
- ExpressVPN. (n.d.). What Is a VPN? Retrieved May 6, 2021, from https://www.expressvpn.com/what-is-vpn
- Nate Lord. (2017, December 5). Oversharing: Your Biggest Security Risk Could be You (Infographic). Retrieved May 6, 2021, from https://digitalguardian.com/blog/oversharing-your-biggest-security-risk-could-be-you-infographic
- Kaspersky. (n.d.). What is VPN? How It Works, Types of VPN. Retrieved May 6, 2021, from https://www.kaspersky.com/resource-center/definitions/what-is-a-vpn
- Kaspersky. (2017, May 17). What is a VPN and Why You Should Use It to Protect Your Privacy. Retrieved May 6, 2021, from https://www.youtube.com/watch?v=wJQndtydiB0
- Cloudflare. (n.d.). Why Use HTTPS? Retrieved May 6, 2021, from https://www.cloudflare.com/learning/ssl/why-use-https/
- Cloudflare. (n.d.). What is HTTPS? Retrieved May 6, 2021, from https://www.cloudflare.com/learning/ssl/what-is-https/
- McAfee. (2017, September 19). Why Software Updates Are So Important. Retrieved May 6, 2021, from https://www.mcafee.com/blogs/consumer/consumer-threat-reports/software-updates-important/
- BBC News. (2021, March 30). Child tweets gibberish from US nuclear-agency account. Retrieved May 6, 2021, from https://www.bbc.com/news/technology-56578544
- TechSoup. (2017, November 3). 9 Tips to Lock Down Your Data and Protect Yourself. Retrieved May 6, 2021, from https://blog.techsoup.org/posts/9-tips-to-lock-down-your-data-and-protect-yourself
- Kaspersky official blog. (2014, February 5). Tip Of The Week: Quick Scan vs Full Scan. Retrieved May 7, 2021, from https://usa.kaspersky.com/blog/tip-of-the-week-quick-scan-vs-full-scan/3131/
- Richard Devine. (2020, December 10). Do you really need PC antivirus software in 2021? Retrieved May 7, 2021, from https://www.windowscentral.com/do-you-need-pc-antivirus
- Harshit Gupta. (2021, February 20). What are the Advantages of Using Antivirus Software? Retrieved May 7, 2021, from https://geekflare.com/advantages-using-antivirus/
- Jennifer Allen. (2020, August 6). 5 reasons you should run an antivirus scan at least once each week. Retrieved May 7, 2021, from https://www.windowscentral.com/5-reasons-you-should-run-antivirus-scan-least-once-each-week
- Kaspersky. (n.d.). What is a Firewall? Retrieved May 7, 2021, from https://usa.kaspersky.com/resource-center/definitions/firewall
- Carol Finch. (n.d.). What Are the Benefits of Clearing the Cache? Retrieved May 7, 2021, from https://smallbusiness.chron.com/benefits-clearing-cache-74960.html
- Andra Zaharia. (2016, July 20). 131 Cybersecurity Tips that Anyone Can Apply. Retrieved May 7, 2021, from https://heimdalsecurity.com/blog/cyber-security-tips/
- David Nield. (2018, November 11). How to Erase, Destroy, and Reuse Old Hard Drives and Phones. Retrieved May 7, 2021, from https://www.wired.com/story/gadget-disposal-safe-secure/
- What Is My IP Address? (n.d.). Here Are Signs You Might Have Been Hacked. Retrieved May 7, 2021, from https://whatismyipaddress.com/hacking-signs
- Kaspersky. (n.d.). Why You Need Backup Files. Retrieved May 7, 2021, from https://www.kaspersky.com/resource-center/preemptive-safety/backup-files

